El Centro de seguridad de Supermicro es la fuente establecida para actualizaciones de seguridad de productos e información de Supermicro, líder mundial en informática empresarial, almacenamiento, redes y tecnología informática ecológica. Nos esforzamos por mejorar continuamente nuestras prácticas de seguridad.
La seguridad de nuestros clientes es una prioridad, por lo que hemos puesto en marcha medidas para salvaguardar el funcionamiento de sus servidores Supermicro y sistemas de almacenamiento. Los servidores y sistemas de almacenamiento, tal y como existen hoy en día, son cada vez más versátiles y a la vez más complejos, por lo que necesitan estar protegidos. Con los actores de amenazas, Supermicro está desarrollando mecanismos de defensa para proteger a los usuarios y clientes y así llevar nuestros conocimientos de seguridad a los más altos de la industria. Supermicro reconoce que los clientes esperan desplegar productos que cumplan con altos estándares de seguridad; por lo tanto, nuestra respuesta está diseñada para el más alto nivel de protección.
Supermicro recomienda seguir las mejores prácticas de seguridad, incluyendo mantener actualizado el sistema operativo y ejecutar las últimas versiones del firmware y de todo el software.
Ciclo de vida de la ciberseguridad Protección de productos
Supermicro ofrece tres productos de servidor fabricados exclusivamente en Estados Unidos. Al centralizar la fabricación en fábricas estadounidenses, se preserva la integridad del sistema. Estos productos "Made in the USA" reducen las posibilidades de intrusión extranjera en la ciberseguridad y están disponibles para clientes de todo el mundo. Para saber más sobre este programa, vaya a la página de la solución Made in the USA.
Supermicro gestiona estrictamente las prácticas de ciberseguridad en todo nuestro sistema de cadena de suministro, para incluir un enfoque más amplio "de la cuna a la tumba" para mantener nuestros productos seguros desde el abastecimiento y la producción, pasando por el funcionamiento, hasta el final natural de la vida útil.
Las mejores prácticas de Supermicro están diseñadas para cumplir los requisitos de seguridad de sus productos, que están respaldados por una amplia funcionalidad y características de seguridad. Estas características garantizan a los clientes que los productos de Supermicro cumplen los estándares de seguridad del sector.
Última actualización:
Supermicro concede la máxima importancia a la seguridad de su centro de datos. Supermicro proporciona una lista de normas y especificaciones para el recién lanzado X14/H14 así como para el X13/H13 y las familias X12/H12 de servidores y sistemas de almacenamiento. Estas capacidades incorporadas le servirán de guía para establecer operaciones seguras en su centro de datos. Revise la siguiente lista.
| Categoría | Especificaciones de seguridad | Productos Intel X14 | Productos AMD H14 | Productos Intel X13 | Productos AMD H13 | Productos Intel X12 | Productos AMD H12 |
|---|---|---|---|---|---|---|---|
| Hardware | La raíz de silicio de la confianza | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Protección contra intrusiones en el chasis | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Módulo de plataforma de confianza (TPM) 2.0 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| BMC TPM1 | ✔ | ✔ | ✔ | ✔ | |||
| Intel Boot Guard | ✔ | ✔ | ✔ | ||||
| Extensiones Intel® de protección de software (Intel® SGX)1 | ✔ | ✔ | ✔ | ||||
| Procesador AMD Secure | ✔ | ✔ | ✔ | ||||
| Cifrado seguro de memoria (SME) AMD | ✔ | ✔ | ✔ | ||||
| Virtualización cifrada segura (SEV) AMD | ✔ | ✔ | ✔ | ||||
| BIOS/BMC | Arranque seguro | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Borrado seguro de la unidad | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Flash seguro | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Actualizaciones seguras del firmware | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Firmware firmado criptográficamente | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| API Redfish segura3 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Seguridad de contraseñas | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Activación/desactivación dinámica USB | ✔ | ✔ | |||||
| Contraseña del disco duro | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Contraseña única BMC | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Recuperación automática del firmware | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Anti-retroceso | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Protecciones BMC en tiempo de ejecución | ✔ | ✔ | ✔ | ✔ | |||
| Bloqueo del sistema | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Seguridad de la cadena de suministro: Atestación a distancia | ✔ | ✔ | ✔ | ✔ | |||
| Gestión de claves de accionamiento (Super-Guardianes) | ✔ | ✔ | ✔ | ✔ | |||
| Bloqueo de usuarios IPMI 2.0 | ✔ | ✔ | ✔ | ✔ | |||
| Supervisión del estado de seguridad | ✔ | ✔ | ✔ | ✔ | |||
| Gestión del Protocolo de Seguridad y Modelo de Datos (SPDM)2 | ✔ | ✔ | ✔ | ✔ | |||
| Normas | NIST SP 800-193 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| NIST SP 800-147b | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| NIST SP 800-88 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
Notas:
- Ciertas características pueden no aplicarse a todos los productos.
- 1 En determinados modelos y configuraciones
- 2 Previsto en Q4 CY2024
- 3 TLS v1.2 / v1.3 soportado. Compatible con RMCP+ Cipher Suite3 / 17
El Baseboard Management Controller (BMC) proporciona acceso remoto a múltiples usuarios en diferentes ubicaciones para la conexión en red. El BMC permite al administrador del sistema supervisar el estado del sistema y gestionar los eventos del ordenador de forma remota. BMC se utiliza con una utilidad de gestión IPMI (Intelligent Platform Management Interface) que permite controlar y supervisar los servidores de forma centralizada. BMC dispone de una amplia gama de funciones de seguridad que responden a las necesidades de los clientes.

Buenas prácticas de seguridad para la gestión de servidores con funciones de BMC habilitadas en centros de datos
Conozca las mejores prácticas de seguridad de BMC
Verificación dinámica de sistemas aprovechando el proceso de certificación
Detecte cualquier cambio en el hardware y el firmware mediante la atestación del sistema
Firmware BMC firmado criptográficamente
Conozca la funcionalidad de seguridad para firmar criptográficamente el firmware del BMC y la BIOS
Función de seguridad de contraseña única de BMC
Sepa cómo beneficiarse de la contraseña única de BMC
Actualización de la plataforma Intel (IPU) 2025.2 Parte 2, agosto de 2025
Esta actualización se aplica a las familias de productos X11, X12 y X13, X14 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01245 - 2025.2 IPU - Aviso sobre el módulo Intel® TDX
- INTEL-SA-01249 - 2025.2 IPU - Aviso sobre la caché de flujo del procesador Intel
Actualización de la plataforma Intel (IPU) 2025.3, agosto de 2025
Esta actualización se aplica a las familias de productos X11, X12 y X13, X14 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01280 - 2025.3 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-01312 - 2025.3 IPU - Aviso sobre el módulo Intel® TDX
- INTEL-SA-01313 - 2025.3 IPU - Aviso sobre el firmware del procesador Intel® Xeon
Vulnerabilidades de seguridad AMD , agosto de 2025
Esta actualización se aplica a las familias de productos H11, H12, H13 y H14 alimentados por 1ª/
- AMD - Vulnerabilidades del cliente AMD - Agosto 2025
- AMD - Vulnerabilidades de los servidores AMD - Febrero de 2025
Boletín de seguridad de AMD AMD, julio de 2025
Supermicro es consciente de las vulnerabilidades de seguridad de ejecución transitoria en algunos procesadores AMD . AMD descubrió varios ataques de canal lateral mientras investigaba un informe de Microsoft® titulado "Enter, Exit, Page Fault, Leak: Testing Isolation Boundaries for Microarchitectural Leaks".
- CVE-2024-36348
- CVE-2024-36349
- CVE-2024-36350
- CVE-2024-36357
2025.1 IPU - Aviso sobre procesadores Intel®, INTEL-TA-01209, junio de 2025
Supermicro es consciente de la vulnerabilidad de seguridad en la que un usuario no cualificado con autenticación de usuario a través del acceso al sistema operativo local puede afectar potencialmente a la disponibilidad (alta) a través de la denegación de servicio mediante la lectura fuera de límites en el firmware para Intel® CSME e Intel® SPS dentro del firmware Intel® PTT.
- CVE-2025-2884
Boletín de seguridad de AMD AMD, junio de 2025
Supermicro es consciente de la vulnerabilidad de seguridad que puede permitir a un atacante privilegiado acceder a los registros del coprocesador Crypto (CCP) de la arquitectura x86. Este problema afecta a los procesadores AMD EPYC™ de 1ª, 2ª y 3ª generación y a determinadas generaciones de productos H11 y H12.
- CVE-2023-20599
Actualización de la plataforma Intel (IPU) 2025.2, mayo de 2025
Esta actualización se aplica a las familias de productos X11, X12 y X13, X14 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01244 - 2025.2 IPU - Aviso sobre el procesador Intel
- INTEL-SA-01247 - 2025.2 IPU - Aviso sobre el predictor de bifurcación indirecta del procesador Intel
2025.1 IPU - Aviso sobre procesadores Intel®, INTEL-TA-01153, mayo de 2025
Un evento o predicción del procesador puede permitir que se ejecuten operaciones incorrectas (u operaciones correctas con datos incorrectos) de forma transitoria, exponiendo potencialmente los datos a través de un canal encubierto. Es posible que las predicciones de bifurcación indirecta no estén totalmente limitadas por las propiedades IBRS mejoradas y la barrera del predictor de bifurcación indirecta. Esta actualización se aplica a las familias de productos X11, X12 y X13 equipados con procesadores Intel Xeon® y otros procesadores Intel.
Esta vulnerabilidad afecta a la BIOS de Supermicro en determinados productos H13. Supermicro no es consciente de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describe en este aviso.
- INTEL-SA-01153 - 2025.1 IPU - Aviso sobre el procesador Intel
Aviso de seguridad AMI-SA-2025003, marzo de 2025
Supermicro es consciente de una posible vulnerabilidad en el firmware de la BIOS según se informa en el aviso de seguridad AMI-SA202503. Aptio® V contiene una vulnerabilidad en la BIOS por la que un atacante puede provocar una condición de carrera de tiempo de comprobación (TOCTOU) por medios locales. La explotación exitosa de esta vulnerabilidad puede conducir a la ejecución de código arbitrario.
Esta vulnerabilidad afecta a la BIOS de Supermicro en determinados productos H13. Supermicro no es consciente de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describe en este aviso.
- CVE-2024-54084
Boletín de seguridad de AMD AMD, marzo de 2025
Supermicro es consciente del problema de seguridad reportado por Google® conocido como "AMD Microcode Signature Verification Vulnerability" que está causado por una debilidad en el algoritmo de verificación de firmas y la vulnerabilidad podría permitir a un atacante con privilegios de administrador, la capacidad de cargar parches de microcódigo de CPU arbitrarios.
- CVE-2024-36347
Actualización de la plataforma Intel (IPU) 2025.1, febrero de 2025
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01139 - 2025.1 IPU - Aviso sobre el firmware UEFI
- INTEL-SA-01152 - 2025.1 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-01213 - 2025.1 IPU - Aviso sobre Intel® SGX
- INTEL-SA-01228 - 2025.1 IPU - Aviso sobre los procesadores Intel® Core™ de 13ª y 14ª generación
Vulnerabilidades de seguridad AMD , febrero de 2025
Esta actualización se aplica a las familias de productos H12 y H13 alimentados por 1ª/
- AMD - Vulnerabilidades del cliente AMD - Febrero 2025
- AMD - Vulnerabilidades de los servidores AMD - Febrero de 2025
Boletín de seguridad de AMD AMD, febrero de 2025
Supermicro es consciente de la vulnerabilidad de llamada del modo de gestión del sistema (SMM) reportada por Eclypsium en el módulo UEFI AmdPlatformRasSspSmm compatible con múltiples procesadores AMD . Este problema afecta a los procesadores AMD EPYC™ 2nd Gen y a las generaciones de productos H11 y H12.
- CVE-2024-21924
Boletín de seguridad de AMD AMD, febrero de 2025
Supermicro es consciente de las dos vulnerabilidades de seguridad reportadas por Quarkslab dentro de los módulos UEFI AmdPspP2CmboxV2 y AmdCpmDisplayFeatureSMM soportados en múltiples procesadores AMD que podrían permitir a los atacantes ejecutar código dentro de SMM(System Management Mode).Este problema afecta a los procesadores AMD EPYC™ de 1ª, 2ª, 3ª y 4ª generación y a las generaciones de productos H11, H12 y H13.
- CVE-2024-0179
- CVE-2024-21925
Boletín de seguridad de AMD AMD, febrero de 2025
Supermicro es consciente de las vulnerabilidades de seguridad en Power Management Firmware (PMFW), AMD System Management Unit (SMU). Este problema afecta al producto AMD H13 MI300X H13DSG-OM.
- CVE-2024-21927
- CVE-2024-21935
- CVE-2024-21936
Boletín de seguridad de AMD AMD, febrero de 2025
Supermicro es consciente de las vulnerabilidades de seguridad en Power Management Firmware (PMFW), AMD System Management Unit (SMU). Este problema afecta al producto AMD H13 MI300X H13DSG-OM.
- CVE-2024-21971
- CVE-2023-20508
Boletín de seguridad de AMD AMD, febrero de 2025
Supermicro es consciente de la vulnerabilidad de seguridad comunicada por Google® en la que un atacante con privilegios de administrador puede explotar una debilidad en el algoritmo de verificación de firmas y cargar parches de microcódigo de CPU arbitrarios que pueden provocar la pérdida de la protección basada en SEV de un huésped confidencial.
- CVE-2024-56161
Vulnerabilidad en el firmware IPMI de Supermicro BMC, enero de 2025
Se han descubierto varios problemas de seguridad en determinadas placas base Supermicro . Estos problemas afectan al firmware BMC de Supermicro .
- CVE-2024-10237
- CVE-2024-10238
- CVE-2024-10239
Boletín de seguridad de AMD AMD, diciembre de 2024
Supermicro es consciente del problema de seguridad en el que puede ser posible modificar los metadatos de detección de presencia en serie (SPD) para hacer que un módulo de memoria conectado parezca más grande de lo que es, lo que puede producir aliasing de direcciones de memoria. Este problema afecta a los procesadores AMD EPYC™ de 3ª y 4ª generación. placas base. Esta vulnerabilidad afecta a la BIOS de los productos Supermicro H12 y H13.
- CVE-2024-21944
Vulnerabilidad en el firmware IPMI de Supermicro BMC, "Terrapin", octubre de 2024
Se ha descubierto un problema de seguridad en determinadas placas base Supermicro . La vulnerabilidad Terrapin permite a un atacante degradar algoritmos de firma seguros y desactivar medidas de seguridad específicas. El ataque Terrapin requiere un atacante Man-in-the-Middle activo.
- CVE-2023-48795
Vulnerabilidades de la BIOS, septiembre de 2024
Supermicro es consciente de dos vulnerabilidades potenciales en el firmware de la BIOS. Estas vulnerabilidades pueden permitir a un atacante escribir en la SMRAM y secuestrar el RIP/EIP. Afectan a la BIOS de Supermicro en la plataforma Denverton. Supermicro no tiene conocimiento de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describen en este aviso.
- CVE-2020-8738
- CVE-2024-44075
Actualización de la plataforma Intel (IPU) 2024.3, agosto de 2024
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01038 - 2024.2 IPU - Asesoramiento sobre la caché de flujo del procesador Intel® Core™ Ultra
- INTEL-SA-01046 - 2024.2 IPU - Aviso sobre la caché de flujo del procesador Intel
- INTEL-SA-00999 - 2024.3 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-01083 - 2024.3 IPU - Aviso sobre el monitor de transferencia SMI
- INTEL-SA-01100 - 2024.3 IPU - Aviso sobre el procesador Intel® Xeon
- INTEL-SA-01118 - 2024.3 IPU - Aviso sobre procesadores escalables Intel® Xeon® de 3ª generación
Vulnerabilidades de seguridad AMD , agosto de 2024
Esta actualización se aplica a las familias de productos H11, H12 y H13 impulsados por procesadores AMD EPYC™ de 1ª/2ª/3ª/4ª generación. Esta actualización también se aplica a las familias M11/M12 y H13 de productos impulsados por procesadores Ryzen™ Threadripper™. Se descubrieron vulnerabilidades potenciales en varios componentes de la plataforma y se han mitigado en los paquetes AMD EPYC™ y AMD Ryzen™ AGESA™ PI.
- AMD - Vulnerabilidades del cliente AMD - Agosto 2024
- AMD - Vulnerabilidades de los servidores AMD - Agosto de 2024
Boletín de seguridad de AMD AMD, agosto de 2024
Supermicro es consciente de la vulnerabilidad de seguridad por la que un atacante con acceso root puede modificar la configuración del modo de gestión del sistema (SMM) incluso cuando el bloqueo SMM está activado. Este problema afecta a los procesadores AMD EPYC™ de 1ª, 2ª, 3ª y 4ª generación y a las generaciones de productos H11, H12 y H13.
- CVE-2023-31315
Boletín de seguridad de AMD AMD, agosto de 2024
Supermicro es consciente del problema de seguridad por el que un hipervisor malintencionado puede ser capaz de descifrar la memoria de una VM invitada Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) después de que se desactive. Este problema afecta a los procesadores AMD EPYC™ de 3ª y 4ª generación. placas base. Esta vulnerabilidad afecta a la BIOS de los productos Supermicro H12 y H13.
- CVE-2023-31355
- CVE-2024-21978
- CVE-2024-21980
PKFAIL: Vulnerabilidad en el firmware de la BIOS Supermicro , julio de 2024
Supermicro ha solucionado el problema de vulnerabilidad de seguridad conocido como "PKFAIL". Esta nueva vulnerabilidad puede permitir a actores maliciosos lanzar amenazas avanzadas a nivel de firmware desde un sistema operativo. Se determinó que algunos productos Supermicro utilizaban claves de plataforma (PK) inseguras que representan la raíz de confianza para la BIOS. Estas claves inseguras fueron generadas por American Megatrends International (AMI), y fueron suministradas como ejemplo de referencia a Supermicro.
Ver detallesVulnerabilidad "regreSSHion" de OpenSSH, julio de 2024
Se ha descubierto una vulnerabilidad de seguridad con la condición de carrera del manejador de señales críticas en OpenSSH, conocida como "regreSSHion" en el firmware BMC de determinadas placas base Supermicro . Esta vulnerabilidad puede dar lugar a la ejecución remota de código (RCE) no autenticada con privilegios de root.
- CVE-2024-6387
Vulnerabilidades de la BIOS, julio de 2024
Supermicro es consciente de la existencia de posibles vulnerabilidades en el firmware de la BIOS. Estas vulnerabilidades afectan a determinadas placas base X11. Supermicro no es consciente de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describen en este aviso.
- CVE-2024-36432
- CVE-2024-36433
- CVE-2024-36434
Vulnerabilidad en el firmware IPMI de Supermicro BMC, julio de 2024
Se ha descubierto un problema de seguridad en determinadas placas base de Supermicro . Este problema afecta al componente de servidor web de su BMC. Esta vulnerabilidad potencial en el BMC de Supermicro puede provenir de un desbordamiento de búfer en la función "GetValue" del firmware que se produce por una falta de comprobación del valor de entrada.
- CVE-2024-36435
Boletín de seguridad de AMD AMD, junio de 2024
Supermicro es consciente de la debilidad potencial en las funciones de protección SPI de AMD . Este problema afecta a las placas base con procesadores AMD EPYC™ de 1ª, 2ª y 3ª generación. Esta vulnerabilidad afecta a la BIOS de los productos Supermicro H11 y H12.
- CVE-2022-23829
Boletín de seguridad de AMD AMD, mayo de 2024
Supermicro es consciente de las vulnerabilidades de fuga de memoria en el controlador AMD DXE (Drive Execution Environment) en APUs/CPUs móviles y de escritorio de servidor y cliente pueden permitir a un usuario con privilegios elevados obtener información sensible. Este problema afecta a los procesadores AMD EPYC™ de 3ª generación. placas base. Esta vulnerabilidad afecta a la BIOS de los productos Supermicro H12.
- CVE-2023-20594
- CVE-2023-20597
Actualización de la plataforma Intel (IPU) 2024.2, mayo de 2024
Esta actualización se aplica a la familia X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-01036 - 2024.2 IPU - Aviso sobre el software del módulo Intel® TDX
- INTEL-SA-01051 - 2024.2 IPU - Aviso sobre el procesador Intel
- INTEL-SA-01052 - 2024.2 IPU - Aviso sobre el procesador Intel® Core™ Ultra
Vulnerabilidades en el firmware BMC Supermicro , abril de 2024
Se han descubierto varias vulnerabilidades de seguridad en determinadas placas Supermicro . Estos problemas (cross site scripting e inyección de comandos) pueden afectar al componente de servidor web de Supermicro BMC IPMI (Web UI). Se ha creado un firmware BMC actualizado para mitigar estas vulnerabilidades potenciales.
- SMC-2024010010 (CVE: CVE-2024-36430)
- SMC-2024010011 (CVE: CVE-2024-36431)
- SMC-2024010012 (CVE: CVE-2023-33413)
Actualización de la plataforma Intel (IPU) 2024.1 e INTEL-TA-00986, marzo de 2024
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00898 - 2024.1 IPU - Aviso sobre el procesador Intel® Atom
- INTEL-SA-00923 - 2024.1 IPU - Aviso sobre el software del chipset Intel® y el SPS
- INTEL-SA-00929 - 2024.1 IPU - Aviso sobre el BIOS
- INTEL-SA-00950 - 2024.1 IPU OOB - Aviso sobre procesadores Intel
- INTEL-SA-00960 - 2024.1 IPU - Aviso sobre el procesador Intel® Xeon
- INTEL-SA-00972 - 2024.1 IPU - Aviso sobre el bloqueo del bus del procesador Intel
- INTEL-SA-00982 - 2024.1 IPU - Aviso sobre predicciones de retorno de procesadores Intel
- INTEL-SA-00986 - Aviso sobre el procesador Intel® Xeon® de 4ª generación
- INTEL-SA-01045 - 2024.1 IPU OOB - Aviso sobre el procesador Intel® Xeon® D
Boletín de seguridad de AMD AMD, febrero de 2024
Supermicro es consciente de las vulnerabilidades de los procesadores AMD . Este problema afecta a los procesadores AMD EPYC™ 1st Gen, AMD EPYC™ 2nd Gen, AMD EPYC™ 3rd Gen y 4th Gen. Esta vulnerabilidad afecta a las placas base Supermicro select H11, H12 y select H13.
- CVE-2023-20576
- CVE-2023-20577
- CVE-2023-20579
- CVE-2023-20587
Boletín de seguridad de AMD AMD, febrero de 2024
Supermicro es consciente de las vulnerabilidades del firmware SEV-SNP. Este problema afecta a los procesadores AMD EPYC™ de 3ª y 4ª generación. Esta vulnerabilidad afecta a las placas base Supermicro select H12 y select H13.
- CVE-2023-31346
- CVE-2023-31347
Vulnerabilidad PixieFAIL, enero de 2024
Supermicro es consciente de una posible vulnerabilidad conocida como "PixieFAIL" en el firmware de la BIOS. Se han descubierto múltiples vulnerabilidades en la pila TCP/IP (NetworkPkg) de Tianocore EDKII, una implementación de código abierto de UEFI. Se trata de nueve vulnerabilidades que, si se explotan a través de la red, pueden provocar la ejecución remota de código, ataques DoS, envenenamiento de la caché DNS y/o la posible fuga de información sensible. PixieFAIL afecta a la BIOS de Supermicro en determinados productos X11, X12, H11, H12, H13 y R12. Supermicro no tiene conocimiento de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describan en este aviso.
- CVE-2023-45229
- CVE-2023-45230
- CVE-2023-45231
- CVE-2023-45232
- CVE-2023-45233
- CVE-2023-45234
- CVE-2023-45235
- CVE-2023-45236
- CVE-2023-45237
Vulnerabilidad LogoFAIL, diciembre de 2023
Supermicro es consciente de una vulnerabilidad potencial conocida como "LogoFAIL" en el firmware de la BIOS. Una validación de entrada inadecuada en una biblioteca de analizador de imágenes utilizada por la BIOS puede permitir a un usuario con privilegios habilitar potencialmente una escalada de privilegios mediante acceso local. LogoFAIL afecta a la BIOS de Supermicro en determinados productos X11, X12, X13, H11, M12 y R12. Supermicro no es consciente de ningún anuncio público o uso malicioso de estas vulnerabilidades que se describe en este aviso.
- CVE-2023-39538
- CVE-2023-39539
Vulnerabilidades en el firmware IPMI de Supermicro BMC, diciembre de 2023
- CVE-2023-33411: IPMI BMC SSDP/UPnP web server directory traversal and iKVM access allowing the rebooting of the BIOS
- CVE-2023-33412: Ejecución remota de comandos de la interfaz web administrativa IPMI BMC disquete virtual/USB
- CVE-2023-33413: Los dispositivos IPMI BMC utilizan claves de cifrado de archivos de configuración codificadas, lo que permite al atacante elaborar y cargar un paquete de archivos de configuración maliciosos para obtener la ejecución remota de comandos.
Boletín de seguridad de AMD AMD
Supermicro es consciente de la vulnerabilidad de seguridad AMD INVD Instruction. Este problema afecta a los procesadores AMD EPYC™ de 1ª generación (SEV y SEV-ES), a los procesadores AMD EPYC™ de 2ª generación (SEV y SEV-ES) y a los procesadores AMD EPYC™ de 3ª generación (SEV, SEV-ES, SEV-SNP). Esta vulnerabilidad afecta a las placas base Supermicro H11 y H12.
- CVE-2023-20592
Actualización de la plataforma Intel (IPU) 2023.4 e INTEL-SA-00950, noviembre de 2023
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00924 - 2023.4 IPU - Aviso sobre el BIOS
- INTEL-SA-00950 - Aviso sobre el procesador Intel
Vulnerabilidades de seguridad AMD , noviembre de 2023
Esta actualización se aplica a las familias de productos H11, H12 y H13 alimentados por 1ª/
- AMD - Vulnerabilidades del cliente AMD - Noviembre 2023
- AMD - Vulnerabilidades de los servidores AMD - Noviembre de 2023
Vulnerabilidades en el firmware IPMI de Supermicro BMC
Se han descubierto varias vulnerabilidades de seguridad en determinadas placas Supermicro . Estos problemas (cross site scripting e inyección de comandos) pueden afectar al componente de servidor web de Supermicro BMC IPMI (Web UI). Se ha creado un firmware BMC actualizado para mitigar estas vulnerabilidades potenciales.
- CVE-2023-40289
- CVE-2023-40284
- CVE-2023-40287
- CVE-2023-40288
- CVE-2023-40290
- CVE-2023-40285
- CVE-2023-40286
Modificación de variables por desbordamiento de pila
Se ha encontrado una vulnerabilidad potencial en el firmware de la BIOS Supermicro Supermicro. Un atacante podría explotar esta vulnerabilidad en las placas base Supermicro manipulando una variable para secuestrar potencialmente el flujo de control, permitiendo a los atacantes con privilegios a nivel del kernel escalar sus privilegios y ejecutar potencialmente código arbitrario.
- CVE-2023-34853
Boletín de seguridad de AMD AMD
Supermicro es consciente del problema del Predictor de Dirección de Retorno, también conocido como "INCEPTION". Este problema afecta a los procesadores AMD EPYC™ de 3ª y 4ª generación. Esta vulnerabilidad afecta a las placas base Supermicro select H12 y select H13.
- CVE-2023-20569
Actualización de la plataforma Intel (IPU) 2023.3, agosto de 2023
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00783 - 2023.2 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-00813 - 2023.2 IPU - Aviso sobre el BIOS
- INTEL-SA-00828 - 2023.2 IPU - Aviso sobre procesadores Intel
- INTEL-SA-00836 - 2023.2 IPU - Aviso sobre procesadores Intel® Xeon® escalables
- INTEL-SA-00837 - 2023.2 IPU - Aviso sobre el procesador Intel® Xeon
Boletín de seguridad de AMD AMD
Supermicro es consciente de la fuga de información entre procesos, también conocida como "Zenbleed". Este problema afecta a los procesadores AMD EPYC™ 7002 también conocidos como procesadores AMD "Zen 2". Esta vulnerabilidad afecta a las placas base Supermicro H11 y H12.
- CVE-2023-20593
Inyección de shell en las notificaciones SMTP
La vulnerabilidad en las tarjetas select supermicro puede afectar a las configuraciones de notificación SMTP. La vulnerabilidad puede permitir a malos actores no autenticados controlar entradas de usuario como el asunto en la configuración de alertas, lo que puede conducir a una ejecución arbitraria de código.
- CVE-2023-35861
Vulnerabilidad reflexiva de amplificación de denegación de servicio (DoS) en el protocolo de localización de servicios SLP
El protocolo de localización de servicios (SLP) permite a un atacante remoto no autenticado registrar servicios arbitrarios. Esto podría permitir al atacante utilizar tráfico UDP falsificado para llevar a cabo un ataque de denegación de servicio (DoS) con un factor de amplificación significativo.
- CVE-2023-29552
Información para los medios: Las claves privadas de Intel BootGuard OEM han sido potencialmente comprometidas, Mayo 2023
Basándonos en el análisis de cómo Supermicro genera y utiliza las claves privadas, los productos Supermicro no se ven afectados.
Actualización de la plataforma Intel (IPU) 2023.2, mayo de 2023
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00807 - 2023.2 IPU - Aviso sobre el BIOS
Vulnerabilidades de seguridad AMD , mayo de 2023
Esta actualización se aplica a las familias de productos H11, H12 y H13 impulsados por procesadores AMD EPYC™ de 1ª/2ª/3ª/4ª generación. Esta actualización también se aplica a la familia M12 de productos impulsados por procesador Ryzen™ Threadripper™. Se descubrieron vulnerabilidades potenciales en varios componentes de la plataforma y se han mitigado en los paquetes AMD EPYC™ y AMD Ryzen™ AGESA™ PI.
- AMD - Vulnerabilidades del cliente AMD - Mayo 2023
- AMD - Vulnerabilidades del servidor AMD - Mayo 2023
Aviso de SuperDoctor5, marzo de 2023
Los investigadores han identificado una vulnerabilidad en Supermicro SuperDoctor5 (SD5) que puede permitir a cualquier usuario autenticado en la interfaz web ejecutar remotamente comandos arbitrarios en el sistema donde está instalado SuperDoctor5 (SD5).
- CVE-2023-26795
Actualización de la plataforma Intel (IPU) 2023.1, febrero de 2023
Esta actualización se aplica a las familias X11, X12 y X13 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00700 - 2023.1 IPU - Aviso sobre procesadores escalables Intel® Atom® e Intel® Xeon
- INTEL-SA-00717 - 2023.1 IPU - Aviso sobre el BIOS
- INTEL-SA-00718 - 2023.1 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-00730 - 2023.1 IPU - Aviso sobre procesadores escalables Intel® Xeon® de 3ª generación
- INTEL-SA-00738 - 2023.1 IPU - Aviso sobre el procesador Intel® Xeon
- INTEL-SA-00767 - 2023.1 IPU - Aviso sobre procesadores Intel
Módulo regulador de voltaje (VRM) y circuito interintegrado (I²C) sobretensión/subtensión, enero de 2023
Los investigadores han identificado una vulnerabilidad en el controlador de gestión de la placa (BMC) que puede permitir cambios en el voltaje fuera del rango operativo especificado para la CPU y, por tanto, afectar a los cálculos normales.
- CVE-2022-43309
Vulnerabilidades de seguridad AMD , enero de 2023
Esta actualización se aplica a las familias H11 y H12 de productos impulsados por procesadores AMD EPYC™ de 1ª/2ª/3ª/4ª generación. Esta actualización también se aplica a la familia M12 de productos impulsados por procesador Ryzen™ Threadripper™. Se descubrieron vulnerabilidades potenciales en varios componentes de la plataforma y se han mitigado en los paquetes AMD EPYC™ y AMD Ryzen™ AGESA™ PI.
- AMD - Vulnerabilidades del cliente AMD - Enero 2023
- AMD - Vulnerabilidades de los servidores AMD - Enero de 2023
Actualización de la plataforma Intel (IPU) 2022.3, noviembre de 2022
Esta actualización se aplica a las familias X11, y X12 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00610 - 2022.3 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-00668 - 2022.2 IPU - Aviso sobre el BIOS
Aviso de OpenSSL, noviembre de 2022
Las versiones de OpenSSL desde la 3.x hasta la 3.0.6 se encuentran vulnerables a una vulnerabilidad de seguridad de alta gravedad que puede provocar un bloqueo o un comportamiento inesperado. Los productos Supermicro no están afectados por esta vulnerabilidad de OpenSSL.
- CVE-2022-3786
- CVE-2022-3602
Anulación del arranque seguro de Microsoft Windows, agosto de 2022
Los investigadores han identificado varias vulnerabilidades en los cargadores de arranque de terceros de Microsoft que pueden afectar a todos los sistemas informáticos que utilicen x64 UEFI Secure Boot.
- CVE-2022-34301
- CVE-2022-34302
- CVE-2022-34303
Actualización de la plataforma Intel (IPU) 2022.2, agosto de 2022
Esta actualización se aplica a las familias X11, y X12 de productos equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00657 - 2022.2 IPU - Aviso sobre el procesador Intel
- INTEL-SA-00669 - 2022.2 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-00686 - 2022.2 IPU - Aviso sobre el BIOS
Actualización de la plataforma Intel (IPU) 2022.1, junio de 2022
Esta actualización se aplica a las familias de productos X10, X11 y X12 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00601 - 2022.1 IPU - Aviso sobre el BIOS
- INTEL-SA-00613 - 2022.1 IPU - Intel® Boot Guard e Intel® TXT Advisory
- INTEL-SA-00614 - 2022.1 IPU - Aviso sobre Intel® SGX
- INTEL-SA-00615 - 2022.1 IPU - Aviso sobre datos obsoletos de MMIO en procesadores Intel
- INTEL-SA-00616 - 2022.1 IPU - Asesoramiento sobre Intel® Xeon
- INTEL-SA-00617 - 2022.1 IPU - Aviso sobre procesadores Intel
Vulnerabilidades de seguridad AMD , mayo de 2022
Esta actualización se aplica a las familias H11 y H12 de productos impulsados por procesadores AMD EPYC™ de 1ª/2ª/3ª generación. Esta actualización también se aplica a la familia M12 de productos impulsados por procesador Ryzen™ Threadripper™. Se descubrieron vulnerabilidades potenciales en varios componentes de la plataforma y se han mitigado en los paquetes AMD EPYC™ y AMD Ryzen™ AGESA™ PI.
- AMD - Vulnerabilidades del cliente AMD - Mayo 2022
- AMD - Vulnerabilidades de los servidores AMD - Mayo de 2022
Actualización de la plataforma Intel (IPU) Actualización 2021.2, febrero de 2022
Esta actualización se aplica a las familias de productos X10, X11 y X12 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00470 - 2021.2 IPU - Aviso sobre el firmware del chipset Intel
- INTEL-SA-00527 - 2021.2 IPU - Aviso sobre el BIOS
- INTEL-SA-00532 - 2021.2 IPU - Aviso sobre el flujo de control del punto de interrupción del procesador Intel
- INTEL-SA-00561 - 2021.2 IPU - Aviso sobre el procesador Intel
- INTEL-SA-00589 - 2021.2 IPU - Aviso sobre el procesador Intel Atom
Respuesta de Supermicroa la vulnerabilidad de Apache Log4j
Supermicro es consciente y se une a la industria para mitigar la exposición causada por el problema de alta prioridad CVE-2021-44228 (Apache Log4j 2), también acuñado como "Log4Shell", el problema CVE-2021-45046 (Apache Log4j 2) y el problema CVE-2021-45105 (Apache Log4j 2). Supermicro también es consciente de los problemas CVE-2021-4104 y CVE-2019-17571 para Apache Log4j 1.2.
La mayoría de las aplicaciones de Supermicro no se ven impactadas por estas cinco vulnerabilidades. La única aplicación impactada es Supermicro Power Manager (SPM). El problema se abordará en una nueva versión de Supermicro Power Manager (SPM) cuyo lanzamiento está pendiente lo antes posible. SPM vendrá con la versión 2.17.0 de Log4j.
Log4j 2
- CVE-2021-44228
- CVE-2021-45046
- CVE-2021-45105
Log4j 1.2
- CVE-2019-17571
- CVE-2021-4104
Actualización de la plataforma Intel (IPU) 2021.2, noviembre de 2021
Esta actualización se aplica a las familias de productos X10, X11 y X12 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00528 - 2021.2 IPU - Aviso sobre el procesador Intel® Atom
- INTEL-SA-00562 - 2021.1 IPU - Aviso sobre el código de referencia de la BIOS
Vulnerabilidades de seguridad AMD , noviembre de 2021
Esta actualización se aplica a las familias de productos H11 y H12 equipados con procesadores AMD EPYC™ de 1ª/2ª/3ª generación. Se descubrieron vulnerabilidades potenciales en varios componentes de la plataforma y se han mitigado en los paquetes AMD EPYC™ AGESA™ PI.
- AMD - Vulnerabilidades de los servidores AMD - Noviembre 2021
Intel Security Advisory Intel-SA-00525, julio de 2021
- INTEL-SA-00525 - Intel BSSA (BIOS Shared SW Architecture) Aviso DFT
El aviso de seguridad Intel-SA-00525 no afecta a la BIOS Supermicro .
Ver detallesActualización de la plataforma Intel (IPU) 2021.1, junio de 2021
Esta actualización se aplica a las familias de productos X10, X11 y X12 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00442 - 2021.1 IPU - Aviso sobre Intel VT-d
- INTEL-SA-00459 - 2021.1 IPU - Intel-CSME-SPS-TXE-DAL-AMT-Advisory
- INTEL-SA-00463 - 2021.1 IPU - Aviso sobre el BIOS
- INTEL-SA-00464 - 2021.1 IPU - Aviso sobre procesadores Intel
- INTEL-SA-00465 - 2021.1 IPU - Aviso sobre procesadores Intel
Respuesta de Supermicroa la vulnerabilidad Trickboot, marzo de 2021
Supermicro es consciente del problema de Trickboot que se observa sólo con un subconjunto de las placas base X10 UP. Supermicro proporcionará una mitigación para esta vulnerabilidad.
TrickBoot es una nueva funcionalidad dentro del conjunto de herramientas de malware TrickBot capaz de descubrir vulnerabilidades y permitir a los atacantes leer/escribir/borrar la BIOS del dispositivo.
Leer másLa BIOS detecta una vulnerabilidad en el gestor de arranque GRUB2 del sistema operativo Linux, noviembre de 2020
Se ha encontrado un fallo en GRUB2, anterior a la versión 2.06. Un atacante puede utilizar el fallo de GRUB2 para secuestrar y manipular el proceso de verificación de GRUB. BIOS detectará esta condición y detendrá el arranque con un mensaje de error.
- CVE-2020-10713
Actualización de la plataforma Intel (IPU) 2020.2, noviembre de 2020
Esta actualización se aplica a las familias de productos X10, X11 y X12 equipados con procesadores Intel Xeon® y otros procesadores Intel. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- INTEL-SA-00358 - 2020.2 IPU - Aviso sobre el BIOS
- INTEL-SA-00391 - 2020.2 IPU - Aviso sobre Intel® CSME, SPS, TXE y AMT
- INTEL-SA-00389 - 2020.2 IPU - Aviso sobre Intel® RAPL
- INTEL-SA-00390 - Aviso sobre el código de muestra de la plataforma Intel BIOS
Actualización mensual de seguridad de Intel de septiembre de 2020
Esta actualización se aplica a las familias de productos X11 y X12 equipados con procesadores Intel Core®. La actualización de seguridad mensual de septiembre de Intel combina la entrega de actualizaciones de seguridad que pueden haberse proporcionado previamente de forma individual.
Tenga en cuenta que la familia de productos X10 no se ve afectada por este anuncio.
- Intel-SA-00404 - Aviso sobre Intel® AMT e Intel® ISM
Actualización de la plataforma Intel (IPU) 2020.1, junio de 2020
Esta actualización se aplica a las familias de productos X10 y X11 equipados con procesadores Intel Xeon®. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- Intel-SA-00295 - Aviso sobre Intel® CSME, SPS, TXE, AMT y DAL
- Intel-SA-00320 - Aviso sobre el muestreo de datos del búfer de registro especial
- Intel-SA-00322 - Aviso sobre el BIOS de la IPU 2020.1
- Intel-SA-00329 - Aviso sobre fuga de datos en procesadores Intel
- Intel-SA-00260 - Aviso de actualización QSR 2019.2 de los gráficos Intel® para procesadores (actualizado)
Lote 9 de Conformidad ErP (Ecodiseño)
Las regulaciones del Lote 9 son un nuevo conjunto de normas de producto que se ocupan de los dispositivos de almacenamiento de datos, como los servidores de nivel empresarial. Descubra cómo Supermicro cumple los requisitos de diseño ecológico de la Unión Europea (UE) para servidores y productos de almacenamiento como parte de la conformidad con el Lote 9.
Ver detallesActualización mensual de seguridad de Intel de febrero de 2020
Esta actualización se aplica a las familias X11 de productos equipados con procesadores Intel Core®. La actualización de seguridad mensual de febrero de Intel combina la entrega de actualizaciones de seguridad que pueden haberse proporcionado previamente de forma individual.
- Intel-SA-00307 - Escalada de privilegios, denegación de servicio, revelación de información
Actualización del BIOS de Intel, INTEL-SA-00329, enero de 2020
- Intel-SA-00329 - Aviso sobre fuga de datos en procesadores Intel
Actualización de seguridad mensual de diciembre de Intel, diciembre de 2019
Esta actualización se aplica a las familias de productos X10, y X11 equipados con procesadores Intel Xeon®. La actualización de seguridad mensual de diciembre de Intel combina la entrega de actualizaciones de seguridad que pueden haberse proporcionado previamente de forma individual.
- Intel-SA-00289 - Aviso sobre la modificación de la configuración de voltaje de los procesadores Intel
- Intel-SA-00317 - Aviso sobre un fallo de página inesperado en un entorno virtualizado
Actualización de la plataforma Intel (IPU) Actualización 2019.2, noviembre de 2019
Esta actualización se aplica a las familias X10, y X11 de productos equipados con procesadores Intel Xeon®. Intel Platform Update (IPU) combina la entrega de actualizaciones de seguridad que pueden haber sido proporcionadas previamente de forma individual.
- Intel-SA-00164 - Aviso sobre la IPU Intel® Trusted Execution Technology 2019.2
- Intel-SA-00219 - Aviso de actualización de Intel® SGX 2019.2 con IPU para gráficos Intel® para procesadores
- Intel-SA-00220 - Aviso sobre Intel® SGX e Intel® TXT
- Intel-SA-00240 - Aviso de escalada local de privilegios en la CPU de Intel
- Intel-SA-00241 - Intel® CSME, Servicios de plataforma de servidor, Trusted Execution Engine, Intel® Active Management Technology y Dynamic Application Loader 2019.2 IPU Advisory
- Intel-SA-00254 - Aviso sobre la IPU Intel® System Management Mode 2019.2
- Intel-SA-00260 - Aviso sobre la IPU de los gráficos Intel® para procesadores 2019.2
- Intel-SA-00270 - Aviso sobre la interrupción asíncrona de transacciones TSX
- Intel-SA-00271 - Aviso técnico sobre modulación de voltaje
- Intel-SA-00280 - Aviso sobre la IPU del BIOS 2019.2
Actualización de vulnerabilidad de seguridad BMC/IPMI 3 de septiembre de 2019
Los investigadores han identificado varios problemas relacionados con la seguridad en la función Virtual Media de los BMC de Supermicro que requieren una actualización del firmware del BMC para solucionarlos.
CVE-2019-16649
CVE-2019-16650
Vulnerabilidad de seguridad AMD : Virtualización cifrada segura Puntos de curva ECC no válidos (SEV ECC) en la vulnerabilidad del sistema operativo Linux
CVE-2019-9836
Ver detallesVulnerabilidad de seguridad de Intel relativa a un ataque al estilo Rowhammer para filtrar información de ciertos módulos DRAM
Intel-SA-00247 (CVE-2019-0174)
Ver detallesActualización trimestral de seguridad de Intel (QSR) 2019.1, mayo de 2019
Esta actualización se aplica a las familias de productos X8, X9, X10 y X11 equipados con procesadores Intel Xeon®. La publicación trimestral de seguridad (QSR) combina la entrega de actualizaciones de seguridad que pueden haberse proporcionado previamente de forma individual.
- INTEL-SA-00213 (CVE-2019-0089, CVE-2019-0090, CVE-2019-0086, CVE-2019-0091, CVE-2019-0092, CVE-2019-0093, CVE-2019-0094, CVE-2019-0096, CVE-2019-0097, CVE-2019-0098, CVE-2019-0099, CVE-2019-0153, CVE-2019-0170)
- INTEL-SA-00223 BIOS No afectada
- INTEL-SA-00233(CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2019-11091)
Las actualizaciones del BIOS para estos problemas se están desplegando ahora. Consulte a continuación los detalles de los productos afectados y las actualizaciones de BIOS necesarias.
Actualización trimestral de seguridad de Intel (QSR) 2018.4, marzo de 2019
Esta actualización sólo se aplica a la familia de productos X11 con procesadores Intel Xeon®. La publicación trimestral de seguridad (QSR) combina la entrega de actualizaciones de seguridad que pueden haberse proporcionado previamente de forma individual.
- INTEL-SA-00185 (CVE-2018-12188, CVE-2018-12189, CVE-2018-12190, CVE-2018-12191, CVE-2018-12192, CVE-2018-12199, CVE-2018-12198, CVE-2018-12200, CVE-2018-12187, CVE-2018-12196, CVE-2018-12185, CVE-2018-12208)
- INTEL-SA-00191 (CVE-2018-12201, CVE-2018-12202, CVE-2018-12203, CVE-2018-12205, CVE-2018-12204)
"Spoiler Nuevo artículo de investigación sobre la ejecución especulativa en los procesadores Intel
Ver detallesVulnerabilidades de seguridad del controlador de gestión de placa base (BMC) relativas a los sistemas que utilizan los system-on-chips (SoC) AST2400 y AST2500 de ASPEED
- CVE-2019-6260
Ejecución especulativa de canal lateral de Spectre y Meltdown
- Intel SA-00115 (CVE-2018-3639, CVE-2018-3640)
- Intel-SA-00088 (CVE-2017-5715, CVE-2017-5753, CVE-2017-5754)
- Intel-SA-00161 (CVE-2018-3615, CVE-2018-3620, CVE-2018-3646)
Vulnerabilidades de seguridad de Intel relativas a Intel® Management Engine (ME), Intel® Server Platform Services (SPS) e Intel® Trusted Execution Engine (TXE)
- Intel-SA-00086 (CVE-2017-5705, CVE-2017-5708, CVE-2017-5711, CVE-2017-5712, CVE-2017-5706, CVE-2017-5709, CVE-2017-5707, CVE-2017-571000)
BIOS/BMC Firmware Actualizaciones de seguridad anteriores a 2017
Consulte las correcciones de firmware para vulnerabilidades y exposiciones comunes publicadas antes de 2017.
Supermicro trabaja proactivamente con la comunidad de seguridad para identificar y reforzar la seguridad en toda nuestra línea de productos. Encuentre soluciones a los CVE publicados en el firmware Supermicro Supermicro.
Ver detallesPreguntas frecuentes sobre seguridad: Elija la categoría "Seguridad"
Informar de un problema de seguridad del producto
Si ha encontrado un problema de seguridad con un producto Supermicro , envíe un correo electrónico a supermicro con los siguientes detalles:
- Nombre del producto/SKU
- Informe detallado sobre la vulnerabilidad
- Instrucciones para reproducir
- Cualquier CVE relevante
Por favor, no incluya ninguna información sensible o confidencial en correos electrónicos de texto claro - utilice la clave PGP para encriptar su mensaje. El equipo de seguridad de productos de Supermicro revisará su informe y se pondrá en contacto con usted para resolver conjuntamente el problema.
Ver detallesManténgase conectado con las actualizaciones de seguridad de productos de Supermicro
Suscríbase hoy mismo
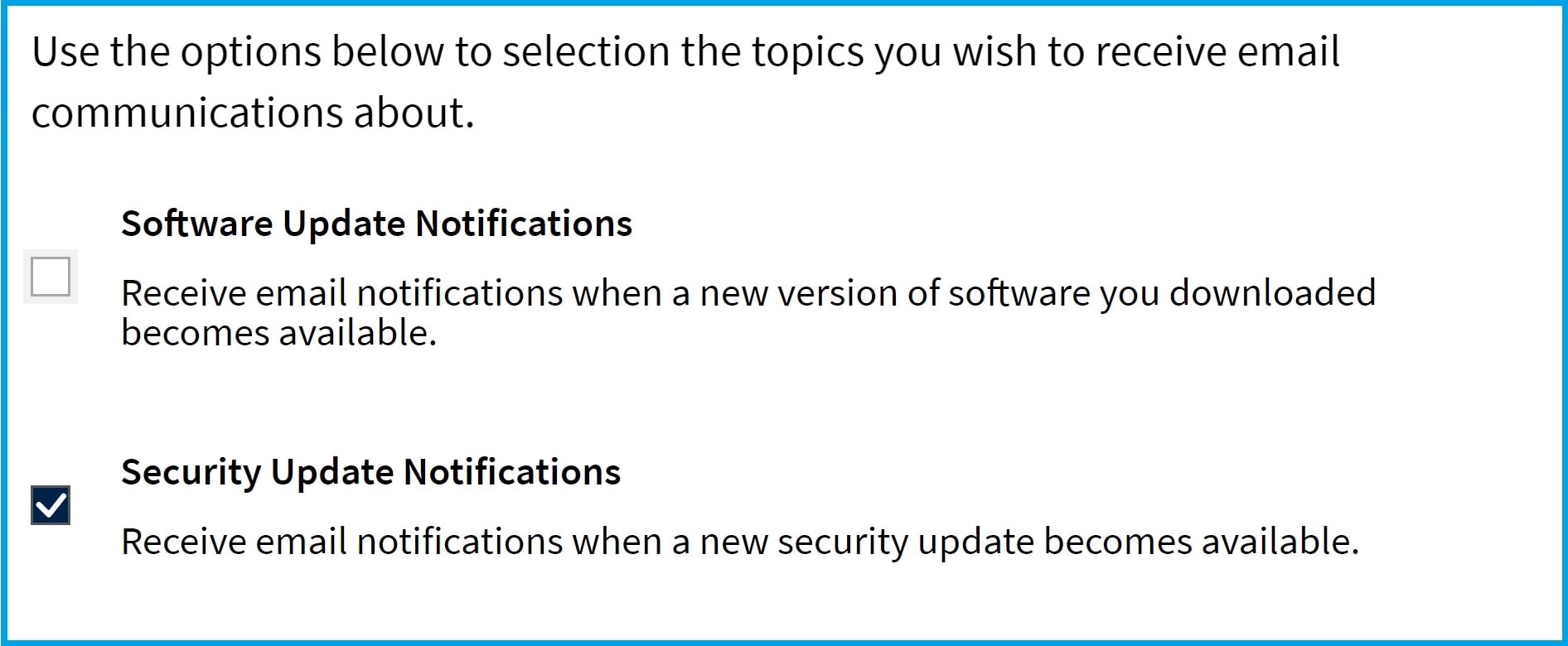
Con el fin de iniciar una suscripción para recibir futuras alertas de seguridad Supermicro por favor siga los siguientes pasos:
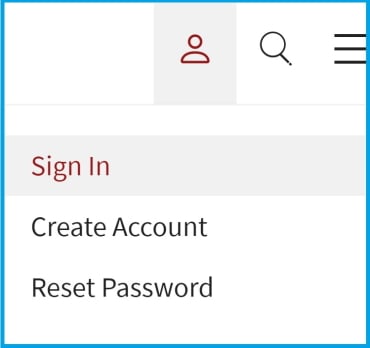
1. Vaya a la parte superior derecha de su pantalla e inicie sesión o cree una cuenta de inicio de sesión único (SSO):
2. Seleccione "Gestionar preferencias de correo electrónico"
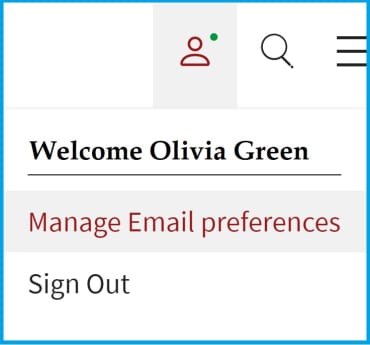
3.Compruebe "Notificaciones de actualizaciones de seguridad"